Portnox Debuts First Cloud-Native IoT Fingerprinting and Profiling Solution
Portnox Debuts First Cloud-Native IoT Fingerprinting and Profiling Solution
Zero Trust Security Leader Brings Lightweight, Easy-to-Use IoT Security Capabilities to the Enterprise and Mid-Market
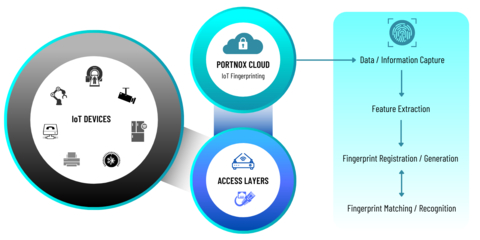
Portnox can now detect and identify all your IoT devices, giving you real-time visibility into every device that’s on your network. No more wondering if that random MAC address is the 3rd floor printer, or a hacker trying to break through the firewall. Easily see the device type, manufacturer, OS, version, and more! We recognize over 260,000 unique IoT device models across 27,000 different brands and 30,000 operating systems, with more being added every day. Portnox NAC-as-a-Service uses multiple different passive fingerprint methods that combine to give us 95% accuracy in profiling IoT devices.
AUSTIN, Texas--(BUSINESS WIRE)--Portnox, a proven leader in cloud-native, zero trust access and endpoint security solutions, today announced the general availability of the first cloud-native IoT security solution to help mid-market and enterprise businesses address rising Internet of Things (IoT) security threats. Now available via the Portnox Cloud, Portnox’s new IoT fingerprinting and profiling capabilities empower organizations to easily and accurately identify, authenticate, authorize, and segment IoT devices across their network to ensure an effective zero trust security posture.
“No organization is immune to the inherent and increasing number of security risks IoT devices pose as they are more susceptible to vulnerabilities and, therefore, prime targets for cyberattacks. Companies of all sizes must properly secure these devices to prevent them from serving as a gateway onto the corporate network by cybercriminals. But as networks become more complex and distributed, and as the number of IoT devices continues to grow, it's becoming more and more difficult to identify and control access for these devices across a given network, let alone secure them,” said Denny LeCompte, CEO at Portnox. “As we bring our vision of simplifying access control and endpoint security for mid-market IT teams to fruition, adding a solution for IoT fingerprinting to our cloud-native platform was the natural next step. Portnox now gives customers full visibility of IoT devices in use across their respective networks.”
Juniper Research predicts that the total number of IoT connections will surge to 83 billion by 2024, while Ponemon Institute found that most (94 percent) organizations think that a security incident related to unsecured IoT devices or applications could be “catastrophic”. Large enterprises are not alone when it comes to rising IoT security headaches – organizations of all sizes are actively trying to strengthen their security postures to account for the surge of threats tied to the rising operational dependence on IoT. With so many IoT devices – printers, cameras, thermostats, sensors, monitors, etc. – now in use across all types of organizations, the ability to automatically onboard and enforce IoT device authentication, control and security policies across the network is mission critical.
Already helping more than 1,000 organizations navigate ever-changing cybersecurity threats, Portnox solutions are purpose-built to be exceptionally easy-to-use, scale, and manage. With the addition of IoT fingerprinting and profiling to the Portnox Cloud, Portnox customers can now enjoy enhanced confidence in the security posture of their network with respect to IoT – without the cost and resource demands associated with traditional on-premise IoT security solutions that can often be complex to configure, deploy, and maintain.
With the latest solution expansion, the Portnox Cloud now provides organizations with:
- Complete device visibility and access policy enforcement across the network for all major device groups – IoT, bring your own device (BYOD) and managed devices
- Enhanced IoT fingerprinting and profiling accuracy powered by artificial intelligence and machine learning
- Strengthened organizational zero trust security postures, accounting for all devices and access layers – on-site and remote
This technology will unlock a tremendous number of additional capabilities, such as automatic policy mapping based on fingerprints and leveraging fingerprinting data to thwart potential MAC Address spoofing risks. Portnox customers can also use fingerprinting information to provide EoL/EoS dates, as well as list potential security vulnerabilities on the endpoint to augment network access and remediation policies.
Portnox continues to rapidly expand its zero trust security offerings across the Portnox Cloud. The company is currently exploring new ways to add agentless risk assessment policy enforcement, as well as data capture options to increase IoT fingerprinting access and automate micro-segmentation and quarantining for IoT devices in future iterations of the solution.
“Providing intelligent insight and visibility into IoT devices connecting to a business’s network with absolutely zero on-prem footprint required is absolutely unprecedented,” said Portnox Vice President of Product Management Jeremy Morrill. “From somewhat basic IP phones, security cameras, printers, TVs and streaming appliances, to complex medical devices and manufacturing equipment, the need for comprehensive IoT security has never been more critical - especially as the proliferation of IP-connected devices continues to accelerate and shows no sign of slowing.”
Effective immediately, IoT fingerprinting and profiling will now be automatically included in Portnox’s NAC-as-a-Service subscription for organizations with 500+ devices. Find more details on pricing packages here or access more product facts here.
About Portnox
Portnox offers cloud-native zero trust access control and cybersecurity essentials that enable agile, resource-constrained IT teams to proactively address today’s most pressing security challenges: the rapid expansion of enterprise networks, the proliferation of connected device types, the increased sophistication of cyberattacks, and the shift to zero trust. Hundreds of companies have leveraged Portnox’s award-winning security products to enforce powerful network access, endpoint risk monitoring and remediation policies to strengthen their organizational security posture. By eliminating the need for any on-premises footprint common among traditional information security systems, Portnox allows companies - no matter their size, geo-distribution, or networking architecture - to deploy, scale, enforce and maintain these critical zero trust security policies with unprecedented ease. Portnox has offices in the U.S. and Israel. For information visit www.portnox.com.
Contacts
Media:
Erica Camilo
Connexa Communications
1.610.639.5644
erica@connexacommunications.com