ISACA Survey: IT Security and Risk Experts Share Ransomware Insights in the Aftermath of the Colonial Pipeline Attack
ISACA Survey: IT Security and Risk Experts Share Ransomware Insights in the Aftermath of the Colonial Pipeline Attack
Only 1 in 5 say critical infrastructure organizations should pay ransom if attacked
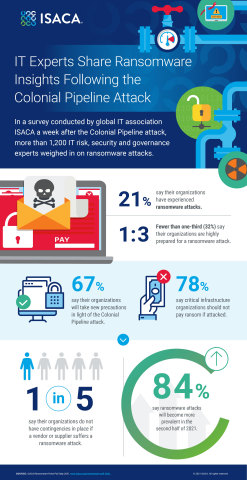
SCHAUMBURG, Ill.--(BUSINESS WIRE)--In the aftermath of the Colonial Pipeline attack, global IT association and learning community ISACA polled more than 1,200 members in the United States and found that 84 percent of respondents believe ransomware attacks will become more prevalent in the second half of 2021.
The Colonial Pipeline attack caused massive disruptions to gasoline distribution in parts of the US this month, resurfacing preparedness for ransomware attacks as a front-burner topic for enterprises around the world.
Colonial reportedly authorized a ransom payment of US $4.4 million.
In the ISACA survey, four out of five survey respondents say they do not think their organization would pay the ransom if a ransomware attack hit their organization. Only 22 percent say a critical infrastructure organization should pay the ransom if attacked.
“In a vacuum, the guidance not to pay makes total sense. We don’t want to negotiate with criminals,” said Dustin Brewer, senior director of emerging technology and innovation at ISACA. “But when you need to get your business back online, a cost/benefit analysis is going to come into play, and a company is going to do what it needs to do to have continuity. Good cyber-hygiene has to be a focus to avoid getting to this point.”
Among the survey’s other findings:
- 85 percent of respondents say they think their organization is at least somewhat prepared for a ransomware attack, but just 32 percent say their organization is highly prepared.
- Four in five respondents say their organization is more prepared for ransomware incidents now than four years ago, when the WannaCry, Petya and NotPetya attacks inflicted major damage. And two-thirds of respondents expect their organization to take new precautions in the aftermath of the Colonial Pipeline incident.
- Nearly half of respondents (46 percent) consider ransomware to be the cyberthreat most likely to impact their organization in the next 12 months.
- Despite the clear risks from ransomware attacks, 38 percent of respondents say their company has not conducted any ransomware training for their staff.
“The fact that more than 80% of organizations are more prepared for ransomware incidents now than they were during the 2017 attacks—and that so many will be taking new precautions after Colonial Pipeline—is wonderful news,” said Brewer. “Open reporting of cyberattacks appears to be working, and in this transparency, we can expect to see newer threats mitigated earlier with faster response times.”
ISACA recommends 10 steps companies can take to be better prepared for, and help prevent, ransomware attacks:
- Understand risk profiles—Organizations should have their risk assessed to accurately prepare for potential attacks. To do this, cybersecurity teams must take inventory of responsibilities, products and services, and the technical requirements affiliated with each. By defining these risk areas, cyberteams can better assess areas that require the most attention when allocating cybersecurity resources.
- Realize data responsibilities—Each employee on a cybersecurity team should realize the types of data that they are responsible for storing, transmitting and protecting.
- Test for incoming phishing attacks—Most attacks start with a phishing campaign, and they continue to be effective. Try testing filters by sending yourself de-weaponized phishing emails identified by others from an external test email account. How often will they make it through? Test it. It is possible that email filters need to be strengthened.
- Assess all cybersecurity roles on a regular, event-controlled basis—Regularly assess and audit cybersecurity controls to ensure that they are applied and maintained appropriately. A truly mature organization will test these controls on both a time-based schedule and in response to incidents.
- Evaluate patches on a timely basis—Ensure that patches are applied in an organized and methodical fashion. For vulnerable legacy systems that cannot be patched or updated, isolate them in the network and ensure that those systems do not have access to the Internet.
- Perform regular policy reviews—Make sure that all pertinent cybersecurity policies not only exist, but are also regularly evaluated and updated based on the ever-changing cybersecurity landscape. Specifically, update these policies based on both time-based schedules and event-based instances.
- Leverage threat intelligence appropriately—Reading and disseminating threat intelligence throughout a cybersecurity team can be overwhelming. Hacks and cyberattacks occur on a 24/7 basis, with different branches of similar attacks emerging overnight in many instances. Understanding which type of intelligence applies to your organization and parsing it out correctly increases understanding of what threats may pose the greatest danger.
- Protect end-user devices—We often forget to ensure 100% protection of end-user devices—not only for devices within the network, but for all devices used by remote users to access systems. Exclusion lists should be minimal.
- Communicate clearly with executive leadership and employees—To gain executive support, ensure that reporting and communication to the leadership level is clear and accurate. Once leadership understands the threat, the risk and its potential impacts, cybersecurity teams are more likely to receive the funding and support required to protect the organization.
- Comprehend organizational cybermaturity—All points listed here are a part of comprehending an organization’s cybermaturity, or its developed defensive readiness against potential cyberattacks and exploitations. Tools like the CMMI Cybermaturity Platform can help organizations understand and improve their cybermaturity.
For more information, see cybersecurity expert and ISACA Emerging Trends Working Group member Chris Cooper’s analysis of the survey results and today’s ransomware landscape here.
About ISACA
ISACA® (www.isaca.org) is a global professional association and learning organization that leverages the expertise of its more than 150,000 members who work in information security, governance, assurance, risk and privacy to drive innovation through technology. It has a presence in 188 countries, including more than 220 chapters worldwide. In 2020, ISACA launched One In Tech, a philanthropic foundation.
Contacts
Emily Van Camp, evcamp@isaca.org, +1.847.385.7223
Kristen Kessinger, communications@isaca.org, +1.847.660.5512