Cequence Report Reveals Retail Fraud Up Nearly 700% as Cybercriminals Exploit Vulnerable Holiday Shopping Season
Cequence Report Reveals Retail Fraud Up Nearly 700% as Cybercriminals Exploit Vulnerable Holiday Shopping Season
New research uncovers heightened cyber risks for retailers as attackers elevate techniques
SUNNYVALE, Calif.--(BUSINESS WIRE)--Cequence Security today released its “2023 Holiday Season API Security Report.” The report found that threat actors are evolving tactics, opting for a more nuanced approach that spreads attacks across a broader timeframe to blend in with legitimate traffic and evade detection ahead of peak holiday shopping times.
Developed by the CQ Prime Threat Research Team, the report is based on real, anonymized traffic and attack data from Cequence’s customer base, comprised of Fortune 500 and Global 2000 companies, and sampled from billions of transactions. It focuses on Cequence’s retail customers in the months leading up to the 2023 holiday season. The CQ Prime team identified and categorized active threats, and the resulting threat intelligence is a foundational element of Cequence products that enable mitigation and blocking to protect customers’ businesses.
“The 2023 holiday season exposed a chilling reality: cybercriminals are employing increasingly sophisticated attack methods and meticulously planning months in advance to exploit vulnerabilities,” said William Glazier, Director of Threat Research at Cequence. “This long-term approach allows them to target unprepared retailers and unsuspecting customers, particularly during peak shopping periods. This shift underscores the urgent need for heightened vigilance and proactive security measures throughout the year.”
Key findings include:
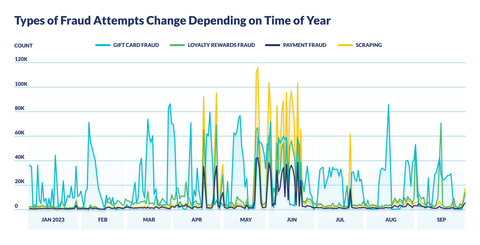
- Pre-Holiday Cyber Onslaught: In the second half of 2023 alone, gift card fraud increased by 110%, while scraping, loyalty card fraud and payment card fraud increased by a collective average of over 700% as attackers lay the groundwork for holiday sale attacks ahead of retailer security crackdowns.
- Rising Threat of Trust-Building Account Takeovers: Account takeovers (ATOs) increased a staggering 410 times for retailers in the second half of the period analyzed (September - November 2023).
- Surge of Automated Line-Jumpers: The report shows that large numbers of products were added to carts via automated tooling to volumetrically flood systems, purchasing as many in-demand items as possible, effectively cornering the market and preventing sales to legitimate customers.
With attackers constantly refining their tactics and expanding their arsenal, the need for a vast, historical threat intelligence database and an expert team to decipher the rapidly evolving API threat landscape has become increasingly paramount. Across their entire customer base, Cequence detected malicious traffic from 719 million unique IP addresses and 325 million malicious login attempts from June to November 2023, highlighting the scale of today’s threats.
“To combat sophisticated threats targeting APIs, today’s organizations must fortify their defenses with a holistic security approach that safeguards their APIs throughout their entire lifecycle,” Glazier continued. “This includes discovering and cataloging all APIs, ensuring rigorous adherence to industry standards, and deploying advanced threat detection and mitigation tools to defend against attacks.”
Additional Resources:
- Download the 2023 Holiday Season API Security Report
- Learn more about our Unified API Protection platform
- Follow us on LinkedIn and Twitter
About Cequence Security
Cequence, a pioneer in API security and bot management, is the only solution that delivers Unified API Protection (UAP), bringing together discovery, compliance, and protection across all internal and external APIs to defend against fraud, business logic attacks, exploits, and unintended data leakage. Needing less than 15 minutes to onboard an API without requiring any instrumentation, SDK, or JavaScript integration, the flexible deployment model supports SaaS, on-premises, and hybrid installations. Cequence solutions scale to handle the most demanding Fortune and Global 2000 organizations, securing more than 8 billion daily API calls and protecting more than 3 billion user accounts across these customers. To learn more, visit www.cequence.ai.
Contacts
Allison Knight
806-570-9819
cequence@10fold.com