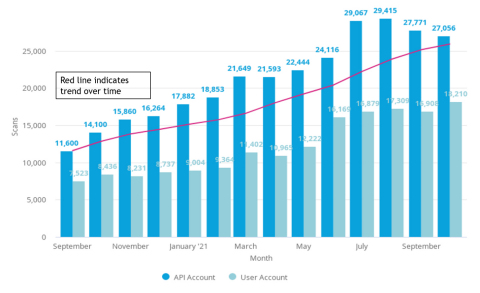
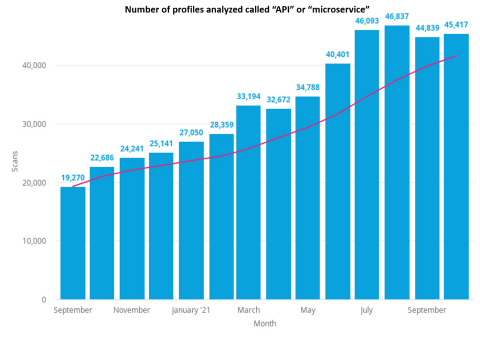
BURLINGTON, Mass.--(BUSINESS WIRE)--Veracode, the largest global provider of application security testing (AST), has revealed usage data that demonstrates cybersecurity is becoming more automated and componentized in line with modern software architectures and development practices. The analysis of 5,446,170 static scans and more than 310,000 apps over a 13-month period from September 2020 to October 2021 found a startling 143 percent growth in the number of small apps, like APIs and microservices, and a 133 percent increase in automated scans run through APIs instead of manually.
Covid-19 has accelerated digital transformation over the past 18 months, and businesses are competing aggressively to be first to market with digital products and services. Pressure on developers to build and deploy software quicker than ever has precipitated the shift to DevSecOps – integrating Development, Security, and Operations to make Application Security an integral part of the software lifecycle. At long last, companies are applying AppSec controls to secure the integrity of the development process, as well as scaling DevSecOps pipeline patterns across the entire enterprise.
“The rise of automation and componentization in software development has driven a sharp increase in the speed and automation of software security as businesses look to AI and machine learning for flaw identification, threat modeling, and remediation,” said Chris Wysopal, Co-Founder & Chief Technology Officer at Veracode. “We’ve already seen DevSecOps grow rapidly in maturity and now there’s an opportunity to shift security even further left into the design phase to become SecDevOps.”
Componentization Drives Speed and Efficiencies
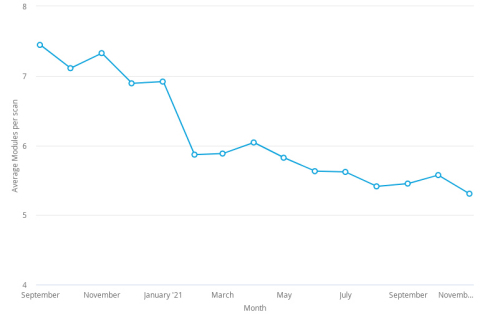
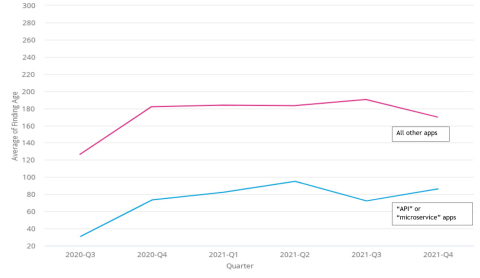
Alongside the upward trajectory in automation, Veracode also found a downward trend in the complexity and size of the code being analyzed, as evidenced by the 30% reduction in the average number of modules scanned per scan, indicating a shift toward scanning of individual components or microservices. This is not surprising considering the rapid adoption of both componentized applications and DevOps practices.
With large applications broken down into small reusable components – or microservices – developers can work in more agile ways to iterate quickly and deliver continuously in increments. Interestingly, the rise of API-first development has actually improved software security, with the average time to fix a flaw reduced by around 50 percent when using static analysis for APIs or microservices. API scanning also enables organizations to find and fix vulnerabilities in APIs as early and efficiently as possible.
Software Security Must Be Pervasive, Not Invasive
With the rising cost and complexity of modern software development practices, businesses will increasingly require a comprehensive, fully integrated security platform with fewer disparate tools. This platform supports pervasive, or continuous, security because it:
- Starts in the design phase with threat modeling, ensuring that only secure components are incorporated into the design. This shifts security even further left so that DevSecOps now becomes SecDevOps ensuring software is ‘secure by design’.
- Is fully integrated, but also open to new technology plugins, to provide comprehensive coverage analyzing every possible dimension of the code. This ‘single pane of glass’ approach empowers security professionals and developers to understand risk, prioritize remediation efforts, and define and monitor progress objectives across multiple dimensions.
- Delivers a frictionless developer experience that enables security analysis to meet developers where they work – within the IDE (Integrated Development Environment), CI/CD (Continuous Integration Continuous Development) pipelines, code and container repositories, and defect tracking systems.
“Recent high-profile attacks, such as the Solar Winds hack, have put the vulnerability of the software supply chain firmly in the spotlight,” Wysopal added. “Businesses now seek the next evolution of software security for peace of mind. This means offering the assurance of continuous orchestration, such as policy definition and management, inline remediation with the ability to ‘self-heal,’ and runtime intelligence that highlights any flaws introduced as underlying components change.”
Given the speed with which software vulnerabilities can develop, demonstrated as recently as the zero-day vulnerability in Log4j 2.x that was discovered last week and is still being exploited, the criticality of continuous security and shifting even further left cannot be underestimated.
About Veracode
Veracode is the leading AppSec partner for creating secure software, reducing the risk of security breach, and increasing security and development teams’ productivity. As a result, companies using Veracode can move their business, and the world, forward. With its combination of process automation, integrations, speed, and responsiveness, Veracode helps companies get accurate and reliable results to focus their efforts on fixing, not just finding, potential vulnerabilities.
Veracode serves thousands of customers worldwide across a wide range of industries. The Veracode solution has assessed more than 45 trillion lines of code and helped companies fix more than 68 million security flaws.
Learn more at www.veracode.com, on the Veracode blog and on Twitter.
Copyright © 2021 Veracode, Inc. All rights reserved. Veracode is a registered trademark of Veracode, Inc. in the United States and may be registered in certain other jurisdictions. All other product names, brands or logos belong to their respective holders. All other trademarks cited herein are property of their respective owners.