NEWTON, Mass. & PETACH TIKVA, Israel--(BUSINESS WIRE)--A new survey released by CyberArk (NASDAQ: CYBR), the global leader in Identity Security, found that 97 percent of senior security executives say attackers are increasingly trying to steal one or more types of credentials. As organizations move assets to the cloud, increase third-party access to corporate resources, and enable sustained remote work models, attackers are targeting non-traditional user populations that may not be adequately protected.
Sponsored by CyberArk, “The CISO View 2021 Survey: Zero Trust and Privileged Access,” demonstrates consensus around the value of Zero Trust and a growing sense of urgency for securing privileged access.
The survey revealed a marked shift in spear-phishing and impersonation attack patterns:
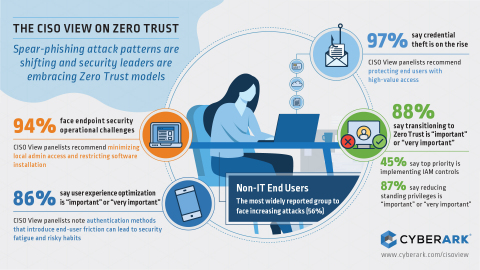
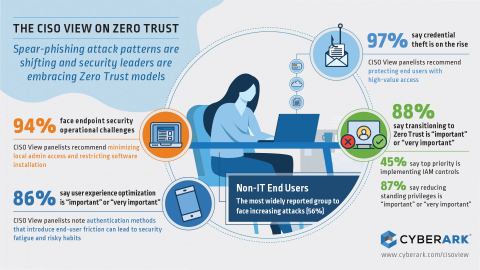
- The most widely reported group facing increased attacks is end-users – including business users with access to sensitive data. A majority of respondents (56 percent) report such users as being increasingly targeted by attackers.
- Attacks are also on the rise against senior leadership (48 percent), third-party vendors and contractors (39 percent), and DevOps and cloud engineers (33 percent).
- Widespread increases in credential theft attempts were reported for personal data (70 percent) and financial systems and data (66 percent). This is clear evidence of attackers’ interest in gaining “high-value” access – access to highly sensitive systems that are often held by end-users rather than administrators for example.
In response to these shifting attack patterns, security leaders are embracing Zero Trust models:
- Eighty-eight (88) percent of respondents said adopting more of a Zero Trust approach is “very important” or “important.”
- To implement a Zero Trust model, the top priority was controls focusing on Identity and Access Management (IAM), chosen by 45 percent of respondents.
- Several types of IAM controls were favored to protect access to sensitive systems. Just-in-time access controls were highly valued, with 87 percent of respondents saying reducing standing privileges is an “important” or “very important” aspect of Zero Trust.
Because attackers recognize the value of non-IT identities and are exploiting weaknesses in protecting these identities because of operational challenges, there is a need for security solutions that work despite internal constraints:
- Endpoint security remains an operational challenge for 94 percent of respondents - 46 percent said that installing and maintaining agents made endpoint security challenging.
- Eighty-six (86) percent said user experience optimization is “important” or “very important,” highlighting a need for security tools and policies that will not be bypassed or ignored due to security fatigue.
“Reverberations from the SolarWinds attack continue to underscore the need to protect privileged credentials and break the attack chain to organizations’ most valuable assets,” said Mike O’Malley, senior vice president, Global Marketing, CyberArk. “As new identities multiply across the enterprise, this survey emphasizes the importance of a Zero Trust-based approach to Identity Security. For security leaders seeking to mitigate the risks of spear-phishing, impersonation attacks and other forms of compromise, we believe the peer experiences captured in the CISO View reports will serve as an invaluable tool, no matter where their organization is on the Zero Trust maturity curve.”
The survey is a companion to “The CISO View: Protecting Privileged Access in a Zero Trust Model.” The fifth in The CISO View series, it is based on in-depth interviews with a panel of 12 top security executives from Global 1000 companies. The panel shared their firsthand experiences around protecting privileged access while transitioning to Zero Trust, including an analysis of risks and recommended controls.
To download the reports and view related materials, visit www.cyberark.com/cisoview.
About the Survey
The CISO View Survey is based on an online survey with 100 security executives from large enterprises conducted in Q4 2020. The CISO View series was developed in conjunction with independent research firm Robinson Insight.
About CyberArk
CyberArk (NASDAQ: CYBR) is the global leader in Identity Security. Centered on privileged access management, CyberArk provides the most comprehensive security offering for any identity – human or machine – across business applications, distributed workforces, hybrid cloud workloads and throughout the DevOps lifecycle. The world’s leading organizations trust CyberArk to help secure their most critical assets. To learn more about CyberArk, visit https://www.cyberark.com, read the CyberArk blogs or follow on Twitter via @CyberArk, LinkedIn or Facebook.
Copyright © 2021 CyberArk Software. All Rights Reserved. All other brand names, product names, or trademarks belong to their respective holders.