DALLAS--(BUSINESS WIRE)--FireHost, the secure cloud hosting company, today announced trends for the attacks it blocked from its clients’ web applications in Q4 2013. FireHost’s IT security experts have noted that the company’s most recent Superfecta* data on attempted cyberattacks could provide evidence of a ‘blackholing’ effect, whereby FireHost’s IP Reputation Management (IPRM) filters have, over time, helped to hide FireHost’s customers’ IPs from would-be hackers.
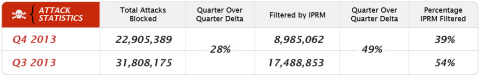
Indeed, the blackholing effect has contributed to the total number of attacks filtered by FireHost’s IPRM dropping from over 17m in Q3 2013 to less than 9m in Q4 2013.
“For anyone new to cybersecurity and threat detection, the blackholing phenomenon must sound incredibly abstract,” admits FireHost founder and CEO Chris Drake. “Thankfully, it’s actually quite simple and our latest statistics certainly quantify the positive benefits this effect has in terms of the protection of regulated data.”
How the blackholing effect works
In a virtualized infrastructure with comprehensive security layers (such as the service provided by FireHost), most of the malicious traffic seen and blocked comes from malevolent networks and botnets. An IP reputation filter intercepts web traffic at the perimeter layer and recognizes when a would-be intruder has been black listed. This means that, when cybercriminals launch web-based attacks or perform reconnaissance on large chunks of the internet from known ‘bad’ IP addresses, the IP reputation filter can prevent them from connecting to a protected network space without reason or response.
Over time, the black hole makes the protected IPs invisible to attackers. As a result, these web applications are exposed to less and less attack traffic, improving memory and processor efficiency as well as reducing network traffic load, to name a few benefits. By the same token, the volume of spam and everything else associated with illegitimate sources also decreases.
“In a conflict zone, hostiles don’t shoot at trees on the off-chance there’s an incredibly well camouflaged infantry unit nearby,” explained FireHost CEO, Chris Drake. “That’s more or less the principle behind the black hole effect. If an automated attack detects a dead address, it’s unlikely to probe it any further. It will simply move on to another, a new vulnerable target, and launch the same attack there.”
Tom Byrnes, CEO of ThreatSTOP, which developed the IP reputation filter FireHost uses to protect its customers, also notes that the decrease in attack traffic could be due to seasonality. “Much like any legitimate corporate industry, cybercrime observes regular business cycles. It’s likely that hackers were mostly targeting consumer applications such as Google and known vulnerable networks such as commodity hosting environments during the last quarter of 2013; this would, in part, account for a decrease in attacks on FireHost’s servers. That said, there’s no doubt that the black hole effect also had a significant impact, with automated attacks unable to recognize the value of FireHost’s IPs.”
Hackers favor the tried and tested
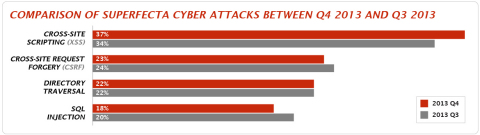
The black hole filtering effect was not the only trend flagged by FireHost’s IT security teams, however. According to Chris Hinkley, CISSP and senior security engineer at FireHost, the fact that the data for Q4 and Q3 2013 was so similar actually says a lot about the current cyber security landscape. Namely that attackers are presently less inclined and less incentivised to develop new attack methods, or at least aren’t creating new malicious tools on a large scale.
“Attackers are still using relatively old attack methods and it’s easy to see why: there’s very little pushback from potential victims and the security industry is struggling to keep up. While new tools and delivery methods are created periodically, recent data breaches such as those suffered by the likes of SnapChat and Target bear proof that old-hat is still good enough. Security measures and countermeasures are not advancing at a quick enough pace to force attackers to be incredibly innovative. There are still many potential victims vulnerable to attack using the same old exploits and tools. Until the information attackers seek is properly protected, and we break out of the status quo, intruders will stick to their favored attacks and do well by them.”
*Superfecta:
The Superfecta consists of four distinct web-application attack types that pose the most serious threat to businesses, comprising Cross-site Request Forgery, (CSRF), Cross-site Scripting (XSS), SQL Injection and Directory Traversal.
Definitions:
- Cross-site Scripting (XSS) – Cross-site scripting involves the insertion of malicious code into webpages in order to manipulate website visitors. It is used by attackers for a range of reasons, from simply interfering with websites to launching phishing attacks against web users.
- Directory Traversal – A Path Traversal attack aims to access files and directories that are stored outside the web root folder.
- Cross-Site Request Forgery (CSRF) – CSRF is an attack that forces an end user to execute unwanted actions on a web application in which he/she is currently authenticated.
- SQL Injection – SQL Injection involves the entering of malicious commands into URLs and text fields on websites that happen to be vulnerable, usually in an attempt to steal the contents of databases storing valuable data such as credit card details or usernames and passwords. The attack vector has been associated with many high profile data breaches.
For more information, please visit: www.firehost.com/superfecta
About FireHost
FireHost offers the most secure, managed, cloud IaaS available, protecting sensitive data and brand reputations of some of the largest companies in the world. With infrastructure built for security, compliance, performance and agility, responsible businesses choose FireHost to reduce risk and improve the collection, storage and transmission of their most confidential, regulated data. FireHost’s sophisticated business continuity solutions allow customers to make proactive choices about distributing application traffic between more than 20 points of presence dispersed across five continents, all while meeting international data protection requirements.
Headquartered in Dallas, FireHost is the chosen secure cloud service provider for brands that won't compromise on the security of their payment card, healthcare and other highly sensitive data. http://www.firehost.com.
Follow FireHost on:
http://www.twitter.com/firehost
http://www.linkedin.com/company/firehost-inc.
http://www.facebook.com/FireHost